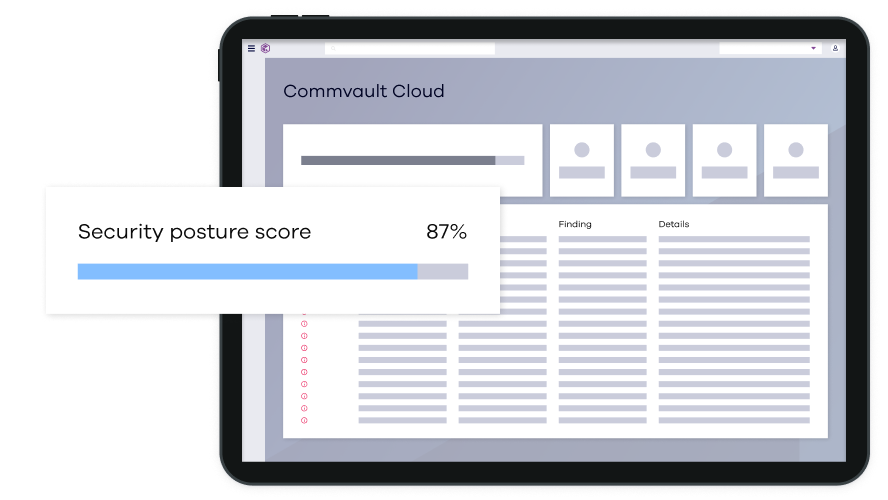
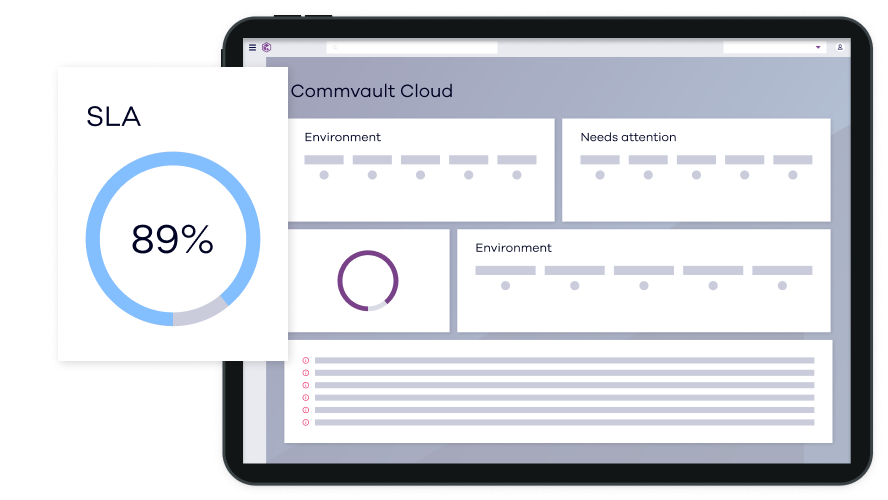
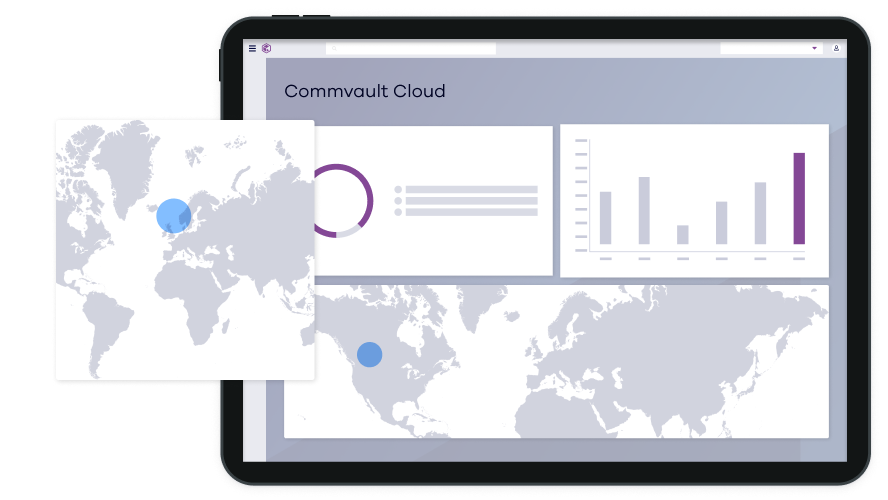
See Threats Sooner – Before Data is Compromised
Uncover and eliminate cyberthreats the moment they begin.

Defend your data. Don’t just recover it. With our Threatwise patented cyber deception technology, you can surface, divert, and respond to threats broadly across production and backup environments.

Early-warning ransomware detection
Detect threats before encryption, exfiltration, or damage. Spot zero-day, silent, and advanced cyberattacks the moment they happen.
See advanced threats sooner
Flag recon, lateral movement,- and unwanted privileged access that bypass conventional security tools.
Reduce response time
Get real-time insight into active and latent threats – without false positives.
Protect your assets
Divert bad actors from critical on-prem, cloud, and backup environments.
ThreatWise
Uncover and eliminate cyberthreats the moment they begin

Bilthoven Biologicals strengthens ransomware protection with Commvault
“With Commvault and Metallic, we can easily manage, protect, and recover data in the cloud and on-premises, even in the worst-case scenario.”
Cyber deception technology redirects and uncovers threats
Indistinguishable decoys
Rapidly deploy authentic threat sensors that mimic real IT, OT, network, and backup assets.
Diversion of bad actors
Bait, lure, and redirect attackers into compromising false resources.
Precision alerts
Get immediate, precise, and early visibility into malicious activity – without false positives.
Instant scale
Deploy and scale in seconds for immediate surface-area coverage.
AI power
Receive guided recommendations for intelligent decoy placement.
Accelerated response
Seamlessly integrate with key security solutions.
Related resources
Explore how Commvault safeguards data from tomorrow’s threats.
Related capabilities
Commvault Threat Scan
Identify backup data threats and eliminate the risk of reinfection to secure, defend and recover data across cloud, on-prem, and SaaS workloads.
Risk Analysis
Get risk governance capabilities that secure and defend sensitive data across your entire infrastructure. Gain visibility into data risks to easily identify and categorize sensitive.
Introducing Commvault® Cloud
The industry’s first platform for true cloud data security. Manage and recover data wherever it lives – with the simplicity and scale of the cloud.

Powered by Metallic® AI
Metallic AI is the engine that drives Commvault Cloud. It leverages a powerful mix of ML and automation that identifies and tags sensitive data using static or dynamic patterns to recognize diverse patterns.
Ready to get started?